What is Biometrics? How is it used in protection?
Biometrics are growing as a sophisticated layer to many personal and organisation safety structures. With the precise identifiers of your biology and behaviors, this may appear foolproof. However, biometric identity has made many careful about its use as standalone authentication.
Modern cybersecurity is targeted on lowering the dangers for this powerful security solution: conventional passwords have long been a factor of weakness for security systems. Biometrics ambitions to reply this trouble via linking evidence-of-identity to our our bodies and behavior styles.
In this newsletter, we’ll explore the basics of how cybersecurity makes use of biometrics. To help destroy matters down, we’ll solution a few common biometrics questions:
What is the meaning of biometric?
What is biometric information?
What is a biometric scanner?
What are the dangers of biometric security?
How can we make biometrics extra at ease?
To begin, permit’s start off with the fundamentals.
What is Biometrics?
For a brief biometrics definition: Biometrics are biological measurements — or physical traits — that may be used to perceive people. For instance, fingerprint mapping, facial reputation, and retina scans are all types of biometric technology, but those are just the maximum diagnosed options.
Researchers declare the shape of an ear, the way a person sits and walks, unique body odors, the veins in a single’s fingers, or even facial contortions are other precise identifiers. These tendencies further outline biometrics.
3 Types of Biometrics Security
While they are able to produce other applications, biometrics have been frequently used in protection, and you may in most cases label biometrics into 3 businesses:
Biological biometrics
Morphological biometrics
Behavioral biometrics
Biological biometrics use traits at a genetic and molecular stage. These may additionally include capabilities like DNA or your blood, which might be assessed through a pattern of your frame’s fluids.
Morphological biometrics involve the structure of your body. More physical trends like your eye, fingerprint, or the form of your face may be mapped for use with security scanners.
Behavioral biometrics are based totally on styles particular to absolutely everyone. How you stroll, talk, or even type on a keyboard may be a demonstration of your identification if these patterns are tracked.
Biometric Security Works
Biometric identification has a developing position in our regular security. Physical characteristics are tremendously constant and individualized — even within the case of twins. Each person’s unique biometric identification may be used to update or at least increase password structures for computer systems, phones, and restrained access rooms and buildings.
Once biometric facts is obtained and mapped, it's miles then saved to be matched with destiny tries at get right of entry to. Most of the time, this information is encrypted and stored within the device or in a far off server.
Biometrics scanners are hardware used to seize the biometric for verification of identity. These scans in shape towards the saved database to approve or deny get admission to to the gadget.
In different words, biometric protection approach your body will become the “key” to unencumber your get admission to.
Biometrics are largely used due to fundamental advantages:
Convenience of use: Biometrics are always with you and can't be lost or forgotten.
Difficult to thieve or impersonate: Biometrics can’t be stolen like a password or key can.
While those structures aren't best, they offer lots of promise for the future of cybersecurity.
Examples of Biometric Security
Here are a few commonplace examples of biometric protection:
Voice Recognition
Fingerprint Scanning
Facial Recognition
Iris Recognition
Heart-Rate Sensors
In exercise, biometric safety has already seen powerful use throughout many industries.
Advanced biometrics are used to protect touchy files and valuables. Citibank already makes use of voice reputation, and the British bank Halifax is trying out gadgets that reveal heartbeat to verify clients' identities. Ford is even considering placing biometric sensors in cars.
Biometrics are incorporated in e-Passports all through the arena. In the US, e-passports have a chip that contains a digital photo of one’s face, fingerprint, or iris, as well as generation that stops the chip from being examine — and the information skimmed — through unauthorized information readers.
As these protection systems are rolled out, we're seeing the pros and cons play out in real-time.
Are Biometric Scanners Safe? - Improvements and Concerns
Biometrics scanners are getting increasingly state-of-the-art. You may even discover biometrics on smartphone security structures. For instance, the facial reputation generation on Apple's iPhone X tasks 30,000 infrared dots onto a person's face to authenticate the person by means of sample matching. The risk of unsuitable identity with the iPhone X biometrics is one in a million, in step with Apple.
The LG V30 smartphone combines facial and voice recognition with fingerprint scanning and continues the data on the cellphone for more security. CrucialTec, a sensor manufacturer, links a coronary heart-charge sensor to its fingerprint scanners for two-step authentication. This facilitates ensure that cloned fingerprints can not be used to get right of entry to its systems.
The task is that biometric scanners, which includes facial popularity structures, can be tricked. Researchers at the University of North Carolina at Chapel Hill downloaded pics of 20 volunteers from social media and used them to assemble 3-D models of their faces. The researchers successfully breached four of the 5 safety structures they examined.
Examples of fingerprint cloning are everywhere. One instance from the Black Hat cybersecurity convention validated that a fingerprint can be cloned reliably in about forty minutes with $10 worth of cloth, definitely by way of making a fingerprint impression in molding plastic or candle wax.
Germany’s Chaos Computer Club spoofed the iPhone’s TouchID fingerprint reader inside days of its launch. The organization sincerely photographed a fingerprint on a tumbler floor and used it to release the iPhone 5s.
Biometrics - Identity & Privacy Concerns
Biometric authentication is convenient, however privacy advocates fear that biometric protection erodes non-public privateness. The problem is that non-public statistics can be gathered easily and with out consent.
Facial reputation is a part of normal life in Chinese towns, where it is used for recurring purchases, and London is famously dotted with CCTV cameras. Now, New York, Chicago, and Moscow are linking CCTV cameras of their cities to facial reputation databases to help neighborhood police combat crime. Ramping up the era, Carnegie Mellon University is growing a digicam which can scan the irises of human beings in crowds from a distance of 10 meters.
In 2018, facial recognition become delivered in Dubai airport, in which tourists are photographed by 80 cameras as they skip through a tunnel in a virtual aquarium.
Facial reputation cameras are also at work in other airports throughout the arena, including the ones in Helsinki, Amsterdam, Minneapolis-St. Paul, and Tampa. All that statistics ought to be saved someplace, fueling fears of regular surveillance and misuse of information…
Biometric Data Security Concerns
A more on the spot trouble is that databases of personal records are targets for hackers. For instance, while the U.S. Office of Personnel Management was hacked in 2015, cybercriminals made off with the fingerprints of 5.6 million authorities personnel, leaving them at risk of identification robbery.
Storing biometric information on a tool – like the iPhone’s TouchID or Face ID – is considered more secure than storing it with a service provider, even if the information is encrypted.
That danger is just like that of a password database, in which hackers may also breach the system and scouse borrow facts that’s not correctly secured. The ramifications, however, are considerably special. If a password is compromised, it may be modified. Biometric statistics, in agreement, remains the same forever.
Ways to Protect Biometric Identity
With the risks to privacy and protection, additional protections must be utilized in biometric structures.
Unauthorized get right of entry to becomes greater tough when systems require multiple manner of authentication, together with existence detection (like blinking) and matching encoded samples to customers within encrypted domain names.
Some security structures additionally encompass additional features, including age, gender, and peak, in biometric data to thwart hackers.
India's Unique ID Authority of India Aadhaar program is a superb instance. Initiated in 2009, the multi-step authentication program includes iris scans, fingerprints from all 10 hands, and facial popularity.
This data is connected to a unique identity card that is issued to every of India's 1.2 billion residents. Soon, this card could be mandatory for each person getting access to social services in India.
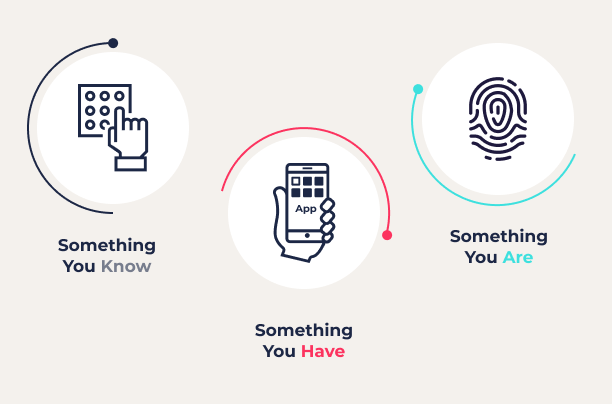
Biometrics make a good alternative for usernames as a part of a -aspect authentication approach. That incorporates:
Something you are (biometrics)
Something you've got (like a hardware token) or something you understand (like a password)
Two-thing authentication makes a powerful mixture, specifically as IoT gadgets proliferate. By layering the protection, secured net gadgets turn out to be less at risk of records breaches.
In addition, using a password supervisor to keep any traditional passwords can give you a further safeguard.
Takeaways on Biometrics
In summary, biometrics stays a growing way to confirm identification for cybersecurity structures.
The mixed protection of your physical or behavioral signatures with other authentications offers a number of the strongest recognized security. At the moment, it is at a minimal higher than the usage of a individual-based totally password as a standalone verification.
Biometric generation offers very compelling solutions for protection. Despite the dangers, the structures are handy and tough to copy. Plus, these structures will hold to develop for a totally long term into the destiny.






Comments
Post a Comment